Using tools and steps listed below we can implement web distribution and Load balancer in AWS and also this will save cost of buying ssl certificate from CA authorized vendors. Instead, it will use certificates provided by Amazon server.
Tools to use AWS CloudFront, Route53, Elastic Load Balancing and AWS Certificate, Manager:
Some key points to keep in mind before following the process:
→ Availability Impact: Possible downtime during DNS changes.
→ Security Impact: SSL needs to be implemented end to end. Certificates generated by AWS Certificate Manager are used on CloudFront and ELB. Self Signed Certificate used on the origin communicating with ELB(Elastic Load Balancing):
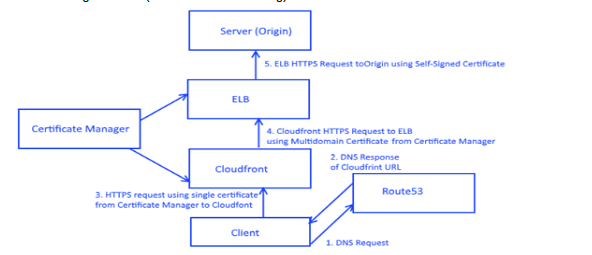
1. A process to generate Self-Signed Server Certificate:
1.1 Generate Certificate:
1.1.1 Generate Key:
openssl genrsa -out multidomain-server-2016.key 2048
1.1.2 Generate CSR:
openssl req -new -key multidomain-server-2016.key -out multidomain-server-2016.csr
1.1.3 Add all domains to file:
echo “subjectAltName=DNS:testdomain.com,DNS:abc.in,DNS:def.gr,DNS:ghi.co.uk,DNS:jkl.eu”>cert_extensions
1.1.4 Generate and Self Sign Certificate:
openssl x509 -req -in multidomain-server-2016.csr -signkey multidomain-server-2016.key -extfile cert_extensions -out multidomain-server-2016.crt -days 3650
1.2 Install Key and Certificate into Apache Virtual Hosts:
Move certificate to /etc/pki/tls/certs/
Move key to /etc/pki/tls/private/
#vi /etc/httpd/conf.d/ssl.conf
DocumentRoot /var/www/html/testdomain
ServerName testdomain.com
SSLEngine on
SSLCertificateFile /etc/pki/tls/certs/multidomain-server-2016.crt
SSLCertificateKeyFile /etc/pki/tls/private/multidomain-server-2016.key
Restart Apache at end of process.
****Note: Restarting Apache will make website unavailable or cause invalid certificate errors on browser unless Elastic Load Balancer is modified to use new cert****
2. Elastic Load Balancer Set up:
2.1 Create Load Balancer: In EC2> Load Balancers click Create Load Balancer and choose Classic Load Balancer:
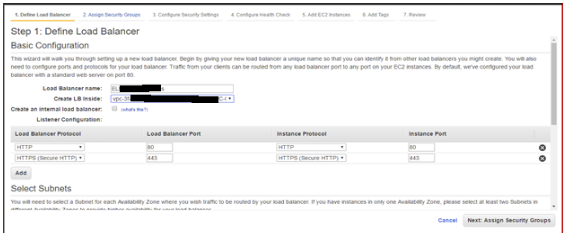
2.2 Define Load Balancer: Give it a name and choose port 80 and port 443 in Listener Configuration:
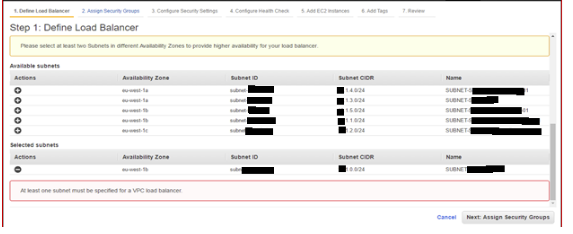
2.3 Choose Subnet:
2.4 Assign Security Group:
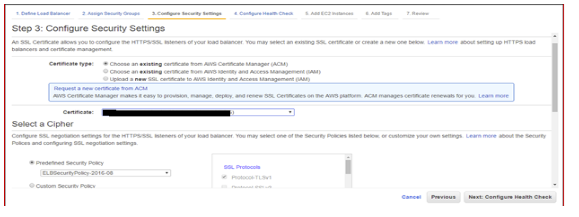
2.5 Define Security Settings:
2.5.1 ACM Certificate: Choose a previously created Certificate from AWS Certificate Manager (ACM). This certificate will need to contain all domain names for all domains. Only one certificate is allowed per load balancer.
Choose Cipher Policy. For PCI, TLSv1 may need to be unchecked:
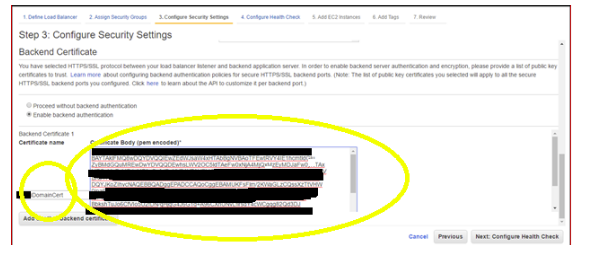
2.5.2 Backend Certificate integration of Load Balancer with Self signed certificate: On the linux server where self-signed certificate was created, get the contents of the self-signed certificate by using less command and copy content.
e.g. less /etc/pki/tls/certs/multidomain-server-2016.crt
On ELB setup, enter any name for the certificate and paste in the contents of the certificate from the server:
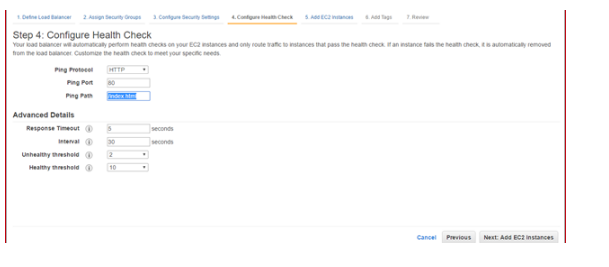
2.6 Configure Health Checks: Make sure file called index.html is on the document root of the linux server (origin – usually /var/www/html/index.htm)
Keep default health check settings:
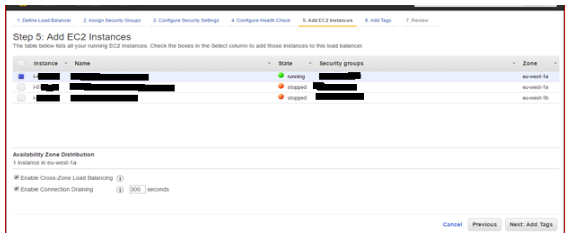
2.7 Add EC2 Instances: Add one or more EC2 Instances. All EC2 Instances must be able to support all hosts defined:
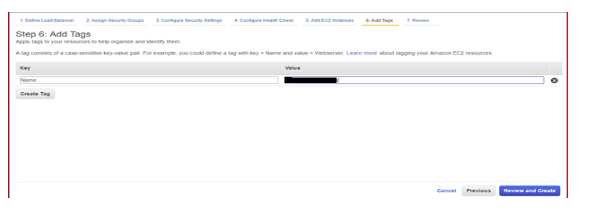
2.8 Add Tags and Review and Create:
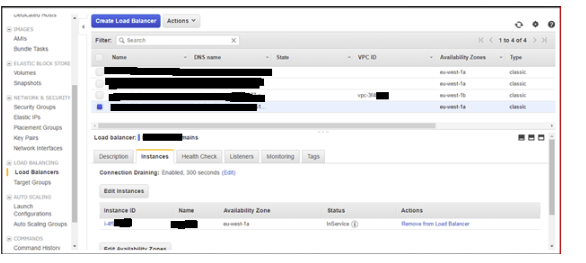
2.9 Check Health: Status needs to be InServi:
3. Cloudfront Setup is required in front of load balancer:
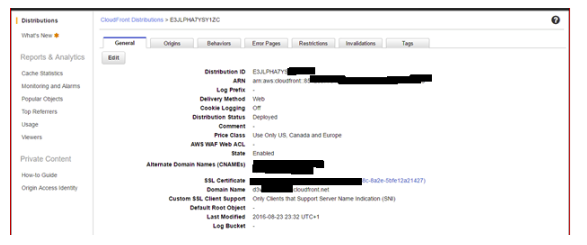
3.1 General Settings:
3.2 Origin Settings: Note, when setting up Origin first, only Load Balancers and S3 buckets are available. If using an EC2 server, paste in the public domain name of the EC2 server. E.g. ec2-54-247-172-106.eu-west-1.compute.amazonaws.com:
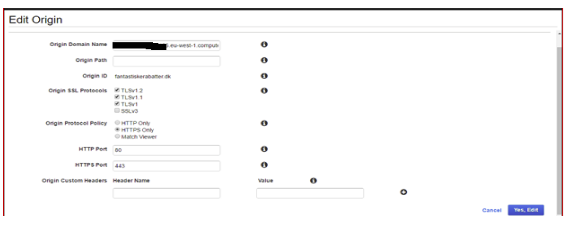
3.3 Behaviours: Important to forward all Headers and Cookies for any sites that are using CNAMEs and cookies respectively:
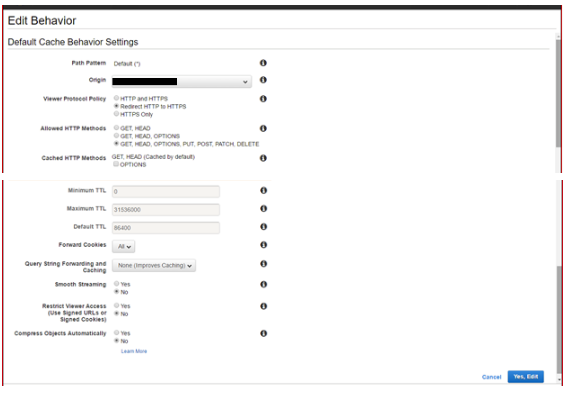
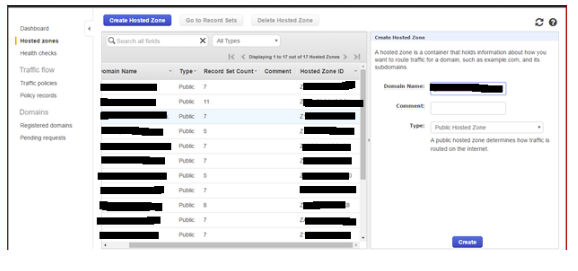
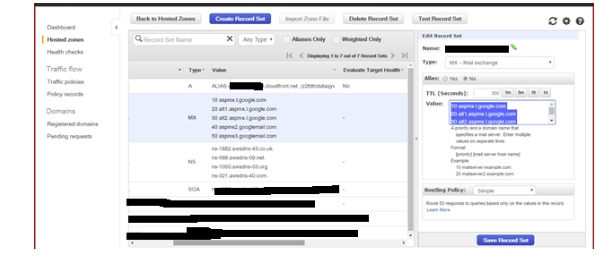
4 Route 53:
4.1 Created hosted zone with the exact name of a top-level domain:
For example,wbd.co.uk:
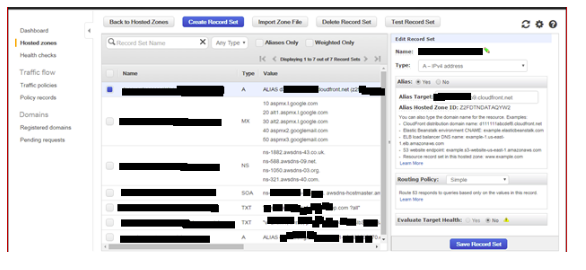
4.2 Records:
4.2.1 A records: To use Cloudfront or an ELB, an alias must be created for the A Record where the target is the CloudFront domain name or ELB name:
4.3 MX records (for example mentioned below):
10 aspmx.l.google.com
20 alt1.aspmx.l.google.com
30 alt2.aspmx.l.google.com
40 aspmx2.googlemail.com
50 aspmx3.googlemail.com
5. Certificate Manager:
5.1 Request Certificate for validation: Enter all domain names required:
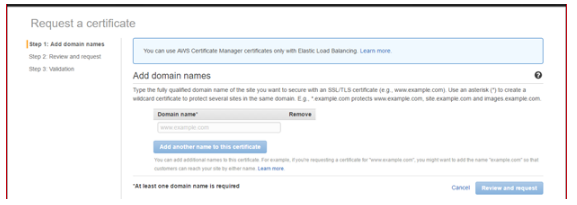
For all domains in the certificate requested, an email is sent to the email address specified in whois and it will pick common addresses such as admin@domain.com and webmaster@domain.com.
